Note: many of the rumblings of this blog post were converted into a formal framework inside AIMOD2. Feel free to check it out!
In Part 3 of the Threat Hunting Shift, I will introduce an Adversarial Framework for Tactical Cyber Defense Operations. Part 4 will complete the introduction to the framework and Part 5 will further delve into the details of it.
I’m a “biggerpicturist” 🪐, I’m always trying to connect the dots in everything I do and this framework is the product of a lot of sense making I’ve been working on for the last 8 months. I am usually talking about crazy shit that mixes cyber security technical knowledge with philosophy, management theories, psychology, knowledge frameworks, etc. You may like it, you may not. But if you can cut through the noise and tune in to the message, you will find a clearing in the woods, I will meet you there.
TL;DR –> If you would like to avoid the philosophical reasons for the threat hunting shift, if you prefer the pure technical details or going straight to the point, you can skip the introductory “yada-yada-oh-la-la-what-the-hell” situation that I’ve got going on here below ;) ;) ;) Go straight to "The 4D: Design, Discover, Disrupt and Defend". Disclaimer: you may still have to connect the dots.
🌅 The Harmonious Image of Cyber Security
Gilles Deleuze, arguably one of the most innovative philosophers of the twentieth century, wrote once a beautiful piece called “The Image of Thought” (Deleuze G. (1994), Difference and repetition (Patton P., Trans.)), where he argues that humanity has been bound to a particular simplistic model of what thinking is, this model remained unquestioned for centuries, assumed to be merely part of common sense. Deleuze challenges the idea that thought is inherently good and naturally inclined towards seeking truth, and instead proposes that thought is centred around the development of problems. He believes that it is through the exploration of these problems that questions are formulated and answers are given. Thought in this sense is not a representation of a pre-given world, but rather the composition of a new world through the activity of thinking. This view of thought contradicts the traditional belief that it is simply a binary game of determining truth and error. Instead, Deleuze asserts that thought is a dynamic and ongoing process of problem-creation and problem-solving. For Deleuze, the problematic is a generative space, the only place where “new” things can emerge. In doing this, he brings attention to our assumed representations, which we take for granted as part of common sense. These assumptions can be limiting and forbid us from exploring new ideas. Can we say the same of our assumptions around how cyber security works?
You all know what I’m talking about, the harmonious image of cyber security is one where conflict in the cybersphere is expressed in terms of protect-allow-restrict. Your business makes up a little digital island, where digital assets are offered to consumers, clients and creators. These assets need to be protected from malicious actors who seek to illegally profit from them. Security comes here to put defensive controls in place, around the different “oasis” of digital services offered to clients and customers. Access to digital goods is allowed or restricted based on identity claims and various authentication and authorization mechanisms. Emergency response and detection processes are in place in case of a security breach. That is it, we have to protect our island.
This is a ’90s view of cyber security that is outdated. We face new problems now, we live in an era of stealth and active cyberwarfare, quantum computing and AI-powered threats. The simplistic idea that we must guard our assets by building a fortress around them and reactively respond to threats as they are detected by our sensors, does not equip today’s businesses to deal with the latest threat landscape.
Today more than ever, our mission is to destroy the harmonic image of the internet and the concept of cyber security around it. We should begin by realizing that our digital asset landscape is a zone of conflict, it is not an oasis anymore, that can be easily protected with a few walls and controls: it is a territory of disputes. If you want your clients and users to enjoy your services, you need to understand the territorial engagement domain that precedes the establishment of any digital business. The problematic is generative.
Your digital asset landscape is a zone of engagement, where territorial disputes between legitimate and illegitimate agents happen all the time. Your strategic objectives are to protect legitimate operations by valid agents, whilst actively disrupting malicious operations that seek to compromise your efforts.
When I think of the above problems, I realize there is an issue that has been bothering me for a while now. I can’t seem to find an integrated model or framework to describe cyber defence operations in terms of this problematic space that makes room for a zone of conflict, that understands defence not merely in terms of protection, but also discovery, engagement and disruption. This is how the 4D framework was born.
🧮 The Framework Design Principles
The Tactical Cyber Defence Operations Framework is meant to be used as a loosely coupled set of practical domains that help describe the tactical activities of cyber defence operations. A tactical framework for cyber defence operations should be concerned with categories of actions that help describe engagement environments that provide guidance for a practical course of action.
The design principles that I attempted to follow when constructing this framework are:
- Abstraction instead of Concretion. The framework needs not be concerned with the particularities of a concrete implementation. By doing this, it remains flexible and adaptable to multiple application approaches.
- Descriptive instead of Prescriptive. The framework does not aim to prescribe what to do, and in which order. Rather, it seeks to provide a descriptive map to help organizations, teams and individuals understand what aspects of a tactical maneuver they are defending against or leveraging to their advantage.
- Polyvalent instead of Monofunctional. The framework can be used to understand defensive cyber operations as much as offensive ones. This means that the framework can be employed to describe adversarial operations whether from the point of view of the attacker, the defender, or both at the same time. In doing this, I’m not trying to aid threat actors, I’m trying to question the naivety by which cyber defence ops merely looks at the protective side, overlooking realistic offensive security scenarios.
- Simple instead of Complicated. The framework aims to be as simple as possible (but not simpler, and also not “simplistic”) and avoid overdetermining its potential applications by overconstraining its own structure. We want to facilitate the possibility of emergence, and for this, we need enabling constraints, as Cynefin would call them.
- Tactical instead of Procedural. The framework should describe tactical environments and the high-level tactics that are most useful and mostly associated with those environments. It should not worry about the techniques or procedures that derive from the different tactics or how they are operationalized.
- Fractality instead of Uniformity (or Monolith). The framework is not supposed to represent a whole, complete model. Instead, it follows the complexity attribute of self-similarity or fractality. Each domain in the framework can virtually replicate the same (or similar) structure at a higher or lower level. For example, when you are in the “Defence” domain, you also have a Design phase, where you configure your protection space and assets, a Disruptive aspect, whereby your defences act as a disruption of the enemy’s forces, a Discovery aspect, by which your defences establish a new lookout zone and expand territorial limits, and a Defence aspect itself, where you protect again what it's already been protected, in a twofold self-reflective move that makes concepts like defence-in-depth (multi-layer protection) possible. The same applies to domains like Discovery, whereby a threat hunting party wouldn’t act recklessly without equipping themselves with the right protections and adopting defensive principles (“don’t run malware on production systems”, etc.) as well as disruptive practices (e.g. cyber deception for adversarial entrapment), etc.
🎛️ The limitations of existing frameworks
There are hundreds of cyber frameworks out there, each of them great when considered within the boundaries of their applicability and the purpose they were developed for. The vast majority of them though are voluminous and detailed, most of the known and best frameworks in the industry are meant to be applied at a policy level by governments and institutions. In contrast, the new framework I’m proposing does not care about implementation details, it is inspired by the Cynefin idea of offering a “sense-making” device, only this time applied to the realm of cyber security.
Let’s quickly summarize why previous frameworks don’t satisfy the design principles:
- MITRE ATT&CK: this framework is probably one of the best tools we have in the cyber security world. The issue with it is, it focuses exclusively on attacker tactics and techniques. It looks at cyber conflict from the point of view of the specific behaviours that adversaries might display. ATT&CK cannot think in terms of the wider picture -and it’s not meant to- like how to embed threat intelligence activities within the model, or how response and hardening have a place.
- MITRE D3FEND: d3fend is another amazing framework which is extremely useful within the confines of countermeasures. It does not, however, offer higher descriptive levels for other aspects of cyber defence operations.
- MITRE ENGAGE: Engage is probably one of the best adversarial engagement frameworks out there, however, its main focus is cyber deception, therefore, it doesn’t concern itself with broader cyber defence ops like emulation, hunting or discovery. Within cyber deception, it is hands down the best operational framework out there!
- NIST Cybersecurity Framework. NIST delves deeply into the details and offers guidelines on outcomes and methodology to assess and manage those outcomes. It is better suited for policy implementations. NIST uses higher-level categories than the MITRE frameworks, including things like Detect and Respond, however, it completely overlooks the role of Deception, Emulation or all of the intel activities related to Discovery.
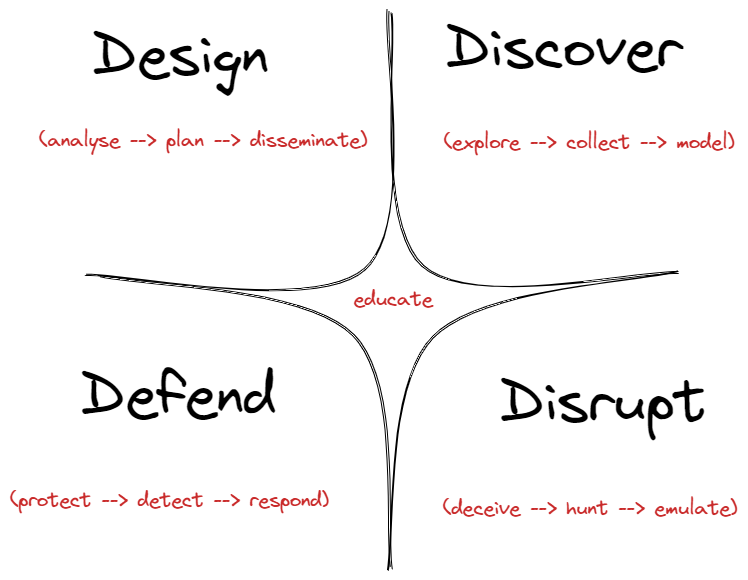
🧬 The 4D: Design, Discover, Disrupt and Defend
The framework is based on 4 pragmatic domains. In Part 3 of the threat hunting shift, we will focus on describing the high-level components of the Discovery and Disruption pragmatic spaces.
Discover
By discovering the enemy’s dispositions and remaining invisible ourselves, we can keep our forces concentrated, while the enemy’s must be divided. (Sun Tzu, The Art of War, Book VI)
Discovery is the domain where information is continuously synthesized into different layers of abstraction to help develop context awareness and insight. The discovery domain is characterized by the simultaneous scouting of known and unchartered territory. Understanding your digital infrastructure, attack surface or external threat landscape is a never ending effort that seeks to survey the technological capabilities, understand weaknesses, secret passages, avenues of exploitation, strengths, natural tendencies, and any traces of adversarial incursion.
Explore
We are not fit to lead an army on the march unless we are familiar with the face of the country—its mountains and forests, its pitfalls and precipices, its marshes and swamps. (Sun Tzu, The Art of War, Book VII)
Exploration refers to the act of searching for and discovering new or unknown things. During exploratory activities, we may have little to no knowledge of the terrain we are venturing into. Our aim is seeking to gain a deeper understanding of the environment that surrounds us and our adversaries. From the point of view of cyber warfare, exploration involves reconnaissance and terrain mapping, the technical process of acquiring information and intelligence about the threat landscape. Exploration may or may not involve collecting data, but data collection is essential to progress to higher levels of information refinement and insight.
Collect
Data collection is the process of gathering, classifying and measuring information on variables of interest, ideally in a systematic fashion, to enable us to answer research questions, test hypotheses, and evaluate outcomes. The data collection process may involve the collection of raw data, as well as the processing, preparation, and analysis of data, in order to make it usable for research purposes. Data collection in cyber defence may encompass activities such as placing sensors in our infrastructure, gathering raw telemetry from digital systems (servers, endpoints, OT devices, etc.), available threat intelligence, internal asset database (CMDB), etc.
The data collection phase is also applicable to GRC (Governance, Risk and Compliance) procedures, like gathering requirements from public policies or stakeholders. Ultimately, the goal of data collection is to obtain accurate and reliable data that can be turned into information and used to answer research questions and inform decision-making. In order to go from data to information, data must be collected and organized in a way that allows it to be analysed and interpreted.
Model
The Discovery domain is not solely concerned with initial exploration and passive data mining. Discovery is also the process of analyzing gathered data and developing models, schemas, frameworks and diagrams that help us make sense of the data that has been collected via exploration. In this phase, we must transition from data to information.
Data is raw, unprocessed facts and figures, while information is data that has been processed and organized in a way that is meaningful and useful. In order to go from data to information, you typically need to perform some kind of modelling and analysis. The process of going from data to information is not just about finding answers, but about creating new questions and possibilities.
Modelling allows us to identify patterns and relationships within the data that might not be immediately obvious. It can also help us make predictions and forecasts. By building a model of how a system is likely to behave, we can make educated guesses about what might happen in the future. Modelling information can be a powerful tool for gaining insights and understanding complex systems.
In the cyber security world, some examples of modelling activity are:
- Analyzing threat intel data to uncover patterns that can be ascribed to a particular threat actor
- Threat Modelling of new systems or apps, to understand how they could be compromised
- Attack Path Modelling, using tools like MITRE Attack Flow, to understand sets of combined attacker behaviours.
Disruption
The supreme art of war is to subdue the enemy without fighting. Thus the highest form of generalship is to balk the enemy’s plans; the next best is to prevent the junction of the enemy’s forces. The third is to attack the enemy’s army in the field before it has formed into order of battle. The fourth is to hurl your army on a single point in the enemy’s line, and the fifth is to roll up his whole line from one end to the other. When he is in disarray, your victory will be complete. (Sun Tzu, The Art of War, Book 3)
Disruption is key to cyber operations. The goal of disruption is to break the patterns that the adversary has memorized, either through purposeful training or repetition arising from environmental constraints. These patterns refer to any aspect of the adversary’s cultural (e.g. the time of the day they operate based on their geographical location and usual work hours in that culture), biological, behavioural or digital (e.g. their botnet infrastructure deployment) disposition. Disruption is the act of using maneuvers to destabilize the opponent to a degree that dismembers their formation leading to imminent defeat. In cyber operations, disruption takes place when the adversary’s capabilities are so impaired that they are forced into a zone of confusion which imposes a high cost of operations whilst attempting to get back into balance. This state of confusion opens a window of opportunity to achieve mission objectives.
The Tao Te Ching offers us one of the most beautiful, powerful, enlightened and insightful teachings of all time when it says “He who conquers others is strong; He who conquers himself is The Strength”. You may as well re-write it by saying He who conquers himself is The Force. Warriors know that to achieve true mastery, we must regard ourselves as our most fearful opponent, we must become our greatest adversary and teacher! Conquering oneself means developing a growth mindset built on resiliency and constant practice, this is the way to self-mastery.
But what does this mean in the context of cyber security? To put it simply, we cannot afford to wait until cybercriminals breach our defenses, we must strive to breach them ourselves first, we cannot afford to wait until nation-state threats compromise our systems: we must relentlessly attempt to compromise them ourselves.
Disruption is about becoming that force able to disrupt our own defensive operations as much as adversarial ones. This requires a huge shift in mindset, from one of passive to one of active defence. This is the road to cyber self-mastery, a transition from simply reacting to and defending against external challenges, to proactively seeking out opportunities to improve and grow: internal motivation instead of merely external. The required shift involves taking a proactive approach to cyber defence development and actively working to identify and address areas of weakness or imbalance. It calls for a willingness to engage with difficult situations, rather than avoiding or denying them.
Some of the ways these weaknesses are uncovered are via emulation of cyber threats: vulnerability scans simulating exploits, tabletop exercises, cyber readiness programs, penetration tests that attempt to find exploitable avenues to existing apps and services, red and purple teaming that mimic real world threat actor behaviours, etc.
Deceive
All warfare is based on deception. Hence, when we are able to attack, we must seem unable; when using our forces, we must appear inactive; when we are near, we must make the enemy believe we are far away; when far away, we must make him believe we are near. (Sun Tzu, The Art of War, Book I)
Deception and subterfuge are essential ingredients to a successful campaign… The warlord of consistent skill never leaves traces of where he has been. He is indistinguishable among the many. (Sun Tzu, The Art of War, Book VI)
Everything starts with deception, a strategy as old as human conflict itself. Deception is the art of influence. Deception is the act of misleading or tricking someone through the use of false or misleading information, concealing one’s true intentions. The goal of deception is to influence adversarial behaviour in order to gain a tactical advantage that helps either disarticulate the opponent’s operations or avoid a negative consequence to our own position and assets.
Deception is an essential activity of the Disruption domain, its goal is to ultimately contribute to the disruption of adversarial operations.
Cyber Deception is essential in cyberwarfare since it can mean the difference between a full breach and just an attempted breach. Cyber Deception takes many different shapes in security operations:
- honey pots
- honey nets (full-scale decoy networks)
- honey tokens (small targeted lures like Azure KeyVault lures, in-memory session credentials for fake accounts, etc.)
- other lures (file)
Deception is accomplished essentially by implementing four components:
- decoy: a fake or imitating object that is used to mislead the target.
- lure: unlike a decoy, a lure is meant to entice or attract the target towards the decoy.
- persona: an analysis of the target, captured for the purposes of running deceptive operations.
- process: an intel-driven process that can deploy and monitor the required infrastructure that ties together the persona, decoy and lure.
Hunt
By holding out advantages to him, he can cause the enemy to approach of his own accord; or, by inflicting damage, he can make it impossible for the enemy to draw near. (Sun Tzu, The Art of War, Book VI)
Appear at points which the enemy must hasten to defend; march swiftly to places where you are not expected. (Sun Tzu, The Art of War, Book VI)
NOTE 👀🌟 *in future iterations of the framework, the "hunt" tactic might be renamed to "engage" or "intercept", still deciding ;)* 👋
Hunting is the art of applying disruption based on threat intelligence
The Disruption domain is characterized by any tactics that aim to actively disrupt cyber operations, either to improve and strengthen them or to dislocate and thwart adversarial campaigns. As such, disruption is also the process of intentionally applying the efforts of other domains (Discovery, Defence, etc.) in a directed way, with the goal to inflict damage on cyber operations. This directed activity is known as hunting or scouting. Hunting has two main purposes that define its tactical goals: interception and coercion.
Threat hunting involves a small team of specialized scouts responsible for surveying the area and providing valuable information about the environment and any potential dangers. Threat hunters should be trained in covert operations and interception tactics and use their skills to gather, distribute, and share critical intelligence about the enemy and the cyber battlefield conditions. Their expertise is crucial in helping to ensure the success of cyber operations.
Threat Hunting requires processing collected data into informational signals. Hunting needs to draw from other domains like “Design”, to develop a higher understanding of the cyber landscape by analyzing available data using aggregation, recombination, clustering and other inference algorithms. The goal of scouting is to intercept adversarial operations to ensure their early disruption, imposing higher operative costs on threat actors’ campaigns. To do this, information needs to be contextualized and applied in a directed effort whose outcome is a higher level of insight.
Hunting as Interception
Interception refers to a type of interference in the trajectory or course of action of an agent or an object. It assumes that there are patterns that threat actors employ, since no one is exempt from them, which end up becoming tendencies that shape a specific course of action. As such, interception aims to stop or interfere with the progress of that chain of events. This can be done in various contexts, such as intercepting an encrypted message being transmitted by a C2, or intercepting a phishing campaign on the build in order to frustrate its success.
Hunting as Coercion
Coercion is the act of imposing constraints either on the adversary or yourself. The aim of a battle is to coerce the opponent into a course of action that destabilizes their plans, defenses and general stance. When directed to adversarial engagement, as opposed to used in a more generic context, coercion takes the shape of deterrence or compellence. The former aims to prevent the other from enacting a course of action, whilst the latter aims to force the other into a defined course of action, usually controlled by the cyber strategist. Both deterrence and compellence intend on influencing the adversary’s behaviour.
An example of coercion in the cyber world would be to develop controlled attack paths in Active Directory and Azure Active Directory. This means, leveraging tools like Bloodhound to (a) understand the current attack paths that could be leveraged to escalate to Domain Admin or similar, (b) craft a fake attack path leveraging deception, which will aim to be the path that threat actors will take, (c) prune your weak attack paths and shape your AD forest to entice (compel) threat actors to take your fake attack path as the easiest one. In executing the above, you will have achieved coercion by compelling cyber adversaries to follow the path of least resistance, one which you control.
Emulate
If you know the enemy and know yourself, you need not fear the result of a hundred battles (Sun Tzu, The Art of War, Book III)
The supreme art of war is to subdue the enemy without fighting (Sun Tzu, The Art of War, Book III)
Emulation refers to the ability of a system to imitate or replicate the functions of another system. Emulation is characterized by what the ancient Greek world called “mimesis” (μίμησις), the act of reproducing or imitating something. Emulation is not a characteristic of computer systems alone, but rather a type of tactic that complex systems employ to dynamically adapt to changing conditions. Think of emulation in the context of history, drama, art, biological organisms, etc.
In the biological world, for example, emulation can occur when one organism imitates or replicates the behaviours, actions, or characteristics of another organism. This can happen for a variety of reasons, such as to gain some advantage in a particular environment or to avoid being targeted by predators.
In this context, imitation can happen when one species closely resembles another species in terms of physical appearance. For example, certain species of butterflies may mimic the appearance of toxic or unpalatable species in order to deter predators. Imitation can also occur when one species observes and copies the behaviours of another species. For example, some primates, such as chimpanzees, have been observed imitating the facial expressions and gestures of their human caregivers.
Emulation can be wide ranging, and applied in multiple contexts, when a child learns to speak from the parents, when on individual learns a behaviour or skill through observation and imitation, etc. We can even talk about “genetic emulation” when one species evolves to closely resemble another species in order to exploit similar ecological niches, like some species of cichlid fish in Africa’s Lake Malawi have evolved to resemble other species in order to better compete for resources.
In the context of cyber security, emulation takes many shapes:
- Vulnerability Scans: when employing technologies that can simulate real exploitation attempts against our systems.
- Red Teaming: simulating real world threat actors in an attempt to compromise our infrastructure and demonstrate feasible attack chains.
- Penetration Testing: simulating application attacks to identify any weaknesses that could be exploited by an attacker, with the goal to determine the security of the system.
References
- Cynefin, a sense-making framework. Cynefin is a framework for understanding what kind of problem space you are in to guide decision-making and action. It was created by David Snowden and takes its name from the Welsh word meaning “the place of your multiple belongings.”, https://cynefin.io/wiki/Cynefin
- Alex S. Wilner (2011) Deterring the Undeterrable: Coercion, Denial, and Delegitimization in Counterterrorism, The Journal of Strategic Studies, 34:1, 3-37, DOI: 10.1080/01402390.2011.541760, https://doi.org/10.1080/01402390.2011.541760
- MITRE ENGAGE, a framework for planning and discussing adversary engagement operations, https://engage.mitre.org/
- MITRE ATT&CK, a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations, https://attack.mitre.org/
- MITRE ATTACK FLOW, a data model with supporting tooling and examples for describing sequences of adversary behaviors. Attack flows help defenders understand, share, and make threat-informed decisions based on the sequence of actions in a cyber-attack., https://ctid.mitre-engenuity.org/our-work/attack-flow/
- MITRE D3FEND, a knowledge graph of cybersecurity countermeasures, https://d3fend.mitre.org/
- Cyber Kill Chain, a model for identification and prevention of cyber intrusions activity, https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html
- NIST, a framework that offers a set of guidelines and best practices for managing cybersecurity risks in organizations, the framework provides a common language and a structured approach for organizations to identify, assess, and manage cybersecurity risks in a consistent and repeatable way, https://www.nist.gov/cyberframework
- Cyber Threat Framework, the Cyber Threat Framework was developed by the US Government to enable consistent characterization and categorization of cyber threat events, and to identify trends or changes in the activities of cyber adversaries, https://www.dni.gov/index.php/cyber-threat-framework