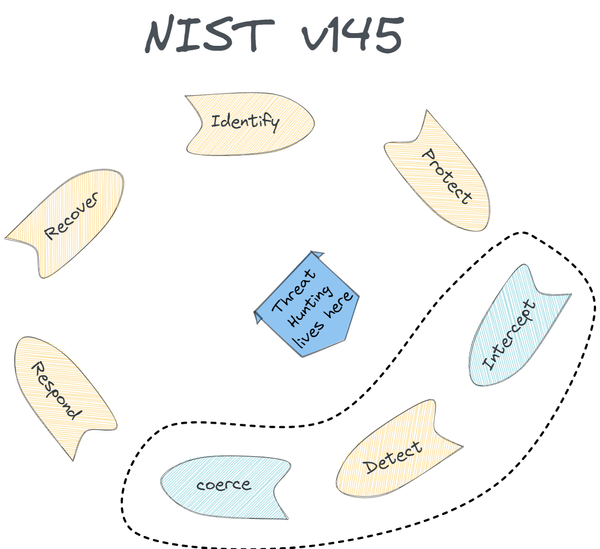
Continuing from Threat Hunting Shift Part 3, we will now introduce the Defend and Design domains. So without further ado, let’s dig into it!
Note: If you haven’t read the previous post, where I present the Discover and Disrupt domains, I advice you head there and give it
cyber defence operations
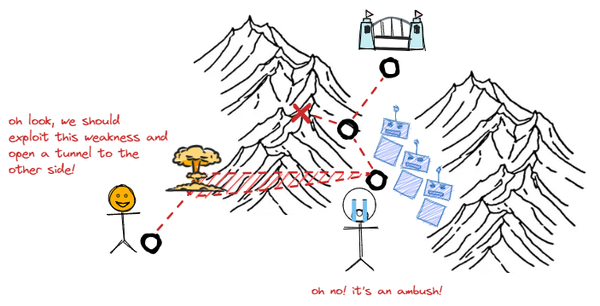
We discuss Active Defense, moving beyond a passive approach to detection. How can we intentionally shape threat actor behavior via Controlled Attack Paths and Cyber Deception? Defenders inadvertently influence attackers by the way they configure layered defenses, impacting attack preferences.
While Threat Hunting is commonly seen as proactive threat detection, we propose a broader approach through the lens of Active Defense. This involves intercepting and disrupting adversaries with the goal of actively shaping attacker behavior rather than relying solely on detection.